02-Week “#Fight the Phish”
From ransomware to SolarWinds, the cybersecurity space has been as hectic as it has ever been over the last two years. For all of the emerging threats cropping up on the horizon, phishing is still one of the oldest forms of threat in cybersecurity. Phishing is continuing to quietly wreak havoc in the cyber community. Despite often being overlooked in terms of hype, phishing has been a mainstay in the cybersecurity threat landscape for decades.
So What Exactly Is Phishing?
Phishing is a cybercrime in which a target or targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords.

With that in mind, what can one do to protect themselves from such a threat? Well here are a few quick best practices and tips for dealing with phishing threats.
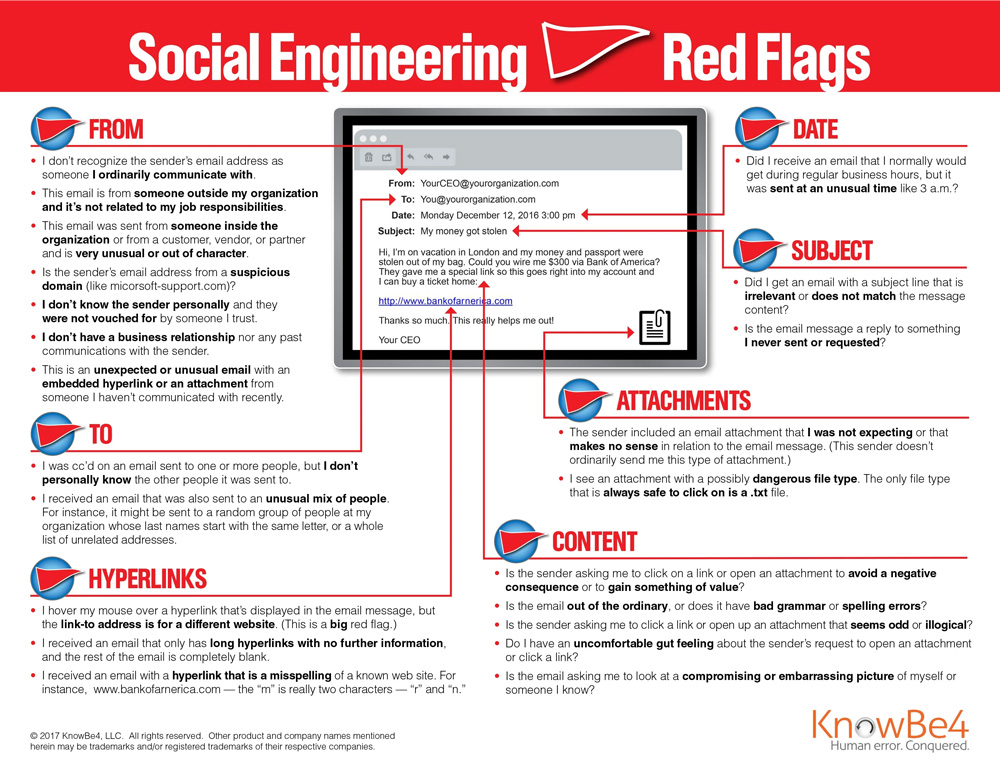
Know the Red Flags
Phishes are masters of making their content and interactions appealing. From content design to language, it can be difficult to discern whether the content is genuine or a potential threat. This is why it is so important to know the red flags.
These are all hallmarks that the content you received could be potentially from phish and indicate that it should be handled with caution.
Verify the Source
Phishing content comes in a variety of ways, however, many phishers will try to impersonate someone you may already know. This could include a colleague, service provider, or friend. This is done as a way to trick you into believing their malicious content is actually trustworthy. Don’t fall for it. If you sense any red flags that something may be out of place or unusual, reach out directly to the individual to confirm whether the content is authentic and safe. If not, break off communication immediately and flag the incident through the proper channels.
Be Aware of Vishing and Other Phishing Offshoots
As more digital natives have come online and greater awareness has been spread about phishing, bad actors have begun to diversify their phishing efforts beyond traditional email. For example, voice phishing or vishing has become a primary alternative for bad actors looking to gain sensitive information from unsuspecting individuals. Similar to conventional phishing, vishing is typically executed by individuals posing as a legitimate organization. An example of this could be a healthcare provider or insurer asking for sensitive information. Simply put, it is imperative that individuals be wary of any sort of communication that asks for personal information whether it be via email, phone, or chat, especially if the communication is unexpected. If anything seems suspicious, again, break off the interaction immediately and contact the company directly to confirm the veracity of the communications.



