Zero Trust Architectures - Foundation of Cyber Hygiene
Zero trust is a paradigm shift in cybersecurity architecture designs that are currently taking shape to combat the ever growing cyber attacks that are increasing in sophistication, varied attack vectors and in coordinated attacks to bring down the major government installations, corporations and even small businesses.
What is Zero Trust Architecture?
It is an end-to-end approach to enterprise computing assets, resources and data security that covers identity and access management, credentials, operations, firewalls and endpoints, hosted environments and interconnecting infrastructure. The focus is on resource protection and physical, virtual or cloud computing assets are never trusted and granted permissions implicitly, but must continually be evaluated and provided access on a need to know basis.
Access is granted to users through a role-based and need-to-know basis. The need-to-know access control leads to context aware security access. Users who require access control that is additional to their role based privileges, are required to request special authorization from their supervisor.
Traditionally, federal agencies, enterprise networks, commercial enterprises, and small businesses, focus on perimeter defense. Authenticated subjects are given authorized access to a broad collection of resources on the internal network, and as a result, unauthorized lateral movement within an environment has become one of the greatest challenges.
Zero Trust (ZT) – ZT is a collection of concepts and ideas designed to minimize uncertainty in enforcing accurate access permission decisions in information systems and services for compromised networks.
Zero Trust Architecture (ZTA) – ZTA is an enterprise cybersecurity plan that utilizes zero trust concepts including component relationships, workflow planning, and access policies. A zero trust enterprise includes physical and virtual network infrastructure as well as operational policies.
Key Elements of Zero Trust Architecture
- All sources that interact with the computing environment are considered resources. Hence the resources need to be trusted at every instance of interaction.
- All communication needs to be secured regardless of the network location for either wired, wireless, connected to a physical network or remote network.
- Access to individual enterprise resources is granted on a per session basis.
- Resource access is implemented by policy, programmatic coding, and through authorization workflows.
- Enterprise wide monitoring of all resources and associated assets for integrity and security postures is enforced.
- All resource authentication and authorization are dynamic and strictly enforced before access is allowed. This is enabled through IAM (Identity and Access Management), password managers to enforce password policy and standards, and resource authorization workflows.
- Collection of information related to computing assets, network infrastructure and inter communications in context to improving the security posture of the organization is critically important to enforce good cyber hygiene.
What does Zero Trust Architecture look like?
The numerous logical components that make up a ZTA deployment in an enterprise can be operated as an on-premise service or through a cloud-based service. The conceptual framework model in the exhibit below shows the basic relationship between the components and their interactions.
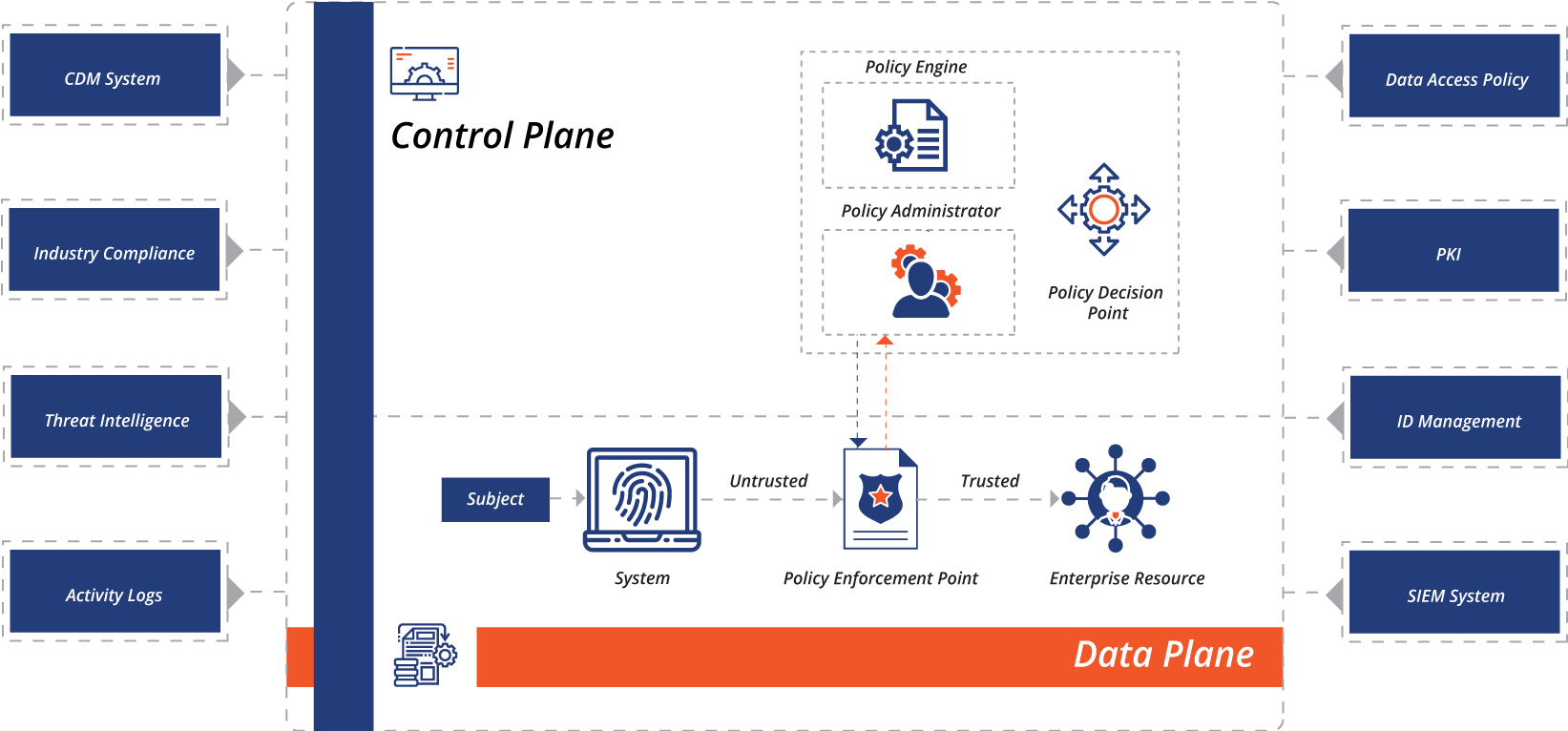
Policy engine (PE): Policy engine determines the decision to grant access to a resource for a given subject. The PE uses enterprise policy as well as data from external sources as input to a trust algorithm which either grants, denies, or revokes access to the resource. The PE is paired with the policy administrator component. The policy engine creates and logs the decision as approved, or denied, and the policy administrator executes the decision.
Policy administrator (PA): is responsible for establishing and shutting down the communication path between a subject and a resource. It would generate any session-specific authentication and authentication token or credential used by a client to access an enterprise resource. It is closely tied to the PE and relies on its decision to ultimately allow or deny a session. If the session is authorized and the request authenticated, the PA configures the PEP to allow the session to start. If the session is denied, the PA signals to the PEP to shut down the connection. The PA communicates with the PEP when creating the communication path. This communication is done via the control plane.
Policy enforcement point (PEP): is responsible for enabling, monitoring, and eventually terminating connections between a subject and an enterprise resource. The PEP communicates with the PA to forward requests and/or receive policy updates from the PA. This is a single logical component in the ZTA, but may be broken into two different components: the client and resource side or a single portal component that acts as a gatekeeper for communication paths. Beyond the PEP is the trust zone hosting the enterprise resource.
Types of Zero Trust Architecture enforcements
There are several ways an organization can implement ZTA for workflows, however each approach implements all tenets of ZT and could focus on any component as the main policy driver.
ZTA using enhanced identity governance
For this approach, enterprise resource access policies are based on identity, assigned attributes, and privileges of the subject. This approach works well with portal access where access privileges play the major role in granting context based-access-control and need-to-know access control.
ZTA using micro segmentation
For this approach the enterprise places infrastructure devices such as intelligent routers or next generation firewalls where Policy Enforcement Point (PEP) is enforced. The advantage with this approach is that the PEP components are managed and should be able to react and reconfigure as needed to respond to threats or change in the workflow.
ZTA Using Network Infrastructure and Software Defined Perimeters
The policy administrator acts as the network controller that sets up and reconfigures the network based on the decisions made by the policy engine (PE). The clients will request access to the applications and domains, and network controllers will grant access via gateways, firewalls and routers. The application network layer will be the most common deployment model using agent/gateway through secure channels. Software defined perimeters are also known as SD-WAN (software defined wide area networks).
Step Ahead Approach to Zero Trust Architecture
Our approach to ZTA is driven by policies, procedures, guidelines, tools and governance.
ZTA Policy Enforcement
Step Ahead Policy enforcement helps an enterprise to remain compliant with all the policy rules including FINRA, HIPAA, PCI-DSS, FISMA, and NIST 800-171. A policy provides the framework for security operations of an enterprise. We do this by developing policies customized to the customer’s nature of business and security posture. Policies can be broken down into data, system, remote, and application access.
Continuous Diagnostics and Mitigation (CDM)
Step Ahead enforces CDM through synchronized security which includes firewall and endpoint device monitoring with asynchronous communication between all end points and the firewall. In the event of a threat, the affected endpoint is immediately isolated from the network, the threat is neutralized and the device is replaced to the network. Intelligent Firewall includes a full suite of built-in analysts for threat hunting, malware analysis, and responding to threats. Threat Intelligence utilizes artificial intelligence, machine learning, and the expertise of malware analysts and data scientists on the team.
Threat intelligence
Step Ahead ensures threat intelligence is enforced through a suite of built in policies as well as customized policies. The policies are enforced in the intelligent firewall, SD-WAN, endpoint device configuration, IAM, and custom integrations.
Secure public key infrastructure (PKI)
Step Ahead uses PKI for generating and logging certificates issued to resources, subjects, services and applications. This also includes the global certificate authority ecosystem and the Federal PKI(FPKI)ꟸ that provides the government with a trust framework and infrastructure to administer digital certificates and public-private key pairs.
System Audits, Network and System Activity Logs
Step Ahead ensures that OS levels, SW patches, application patches and security patches are performed through system audits and asset management software. Network and system activity logs provide key details of threat events, bugs, unauthorized access, and real-time feedback of the security posture of enterprise information systems.
Security information and event management (SIEM) Logs
Through Splunk, Step Ahead integrated SIEM log management into its security management portal. This collects security centric information for later analysis. This data is then used to refine policies and warn of possible attacks against enterprise assets.
IAM System
IAM systems provided by their cloud provider. It is responsible for creating, storing, and managing enterprise user accounts and identity records using a lightweight directory access protocol (LDAP) server. IAM policies, configuration and enforcement are periodically assessed and updated as per company policies.


