Step Ahead OnDemand Services include
Specifically for small and medium sized businesses. It is the simplest way to be compliant with cyber security. Compliance with the NIST 800-171 gives you the peace of mind to operate your business with confidence.
Why Use the Cybersecurity Framework?
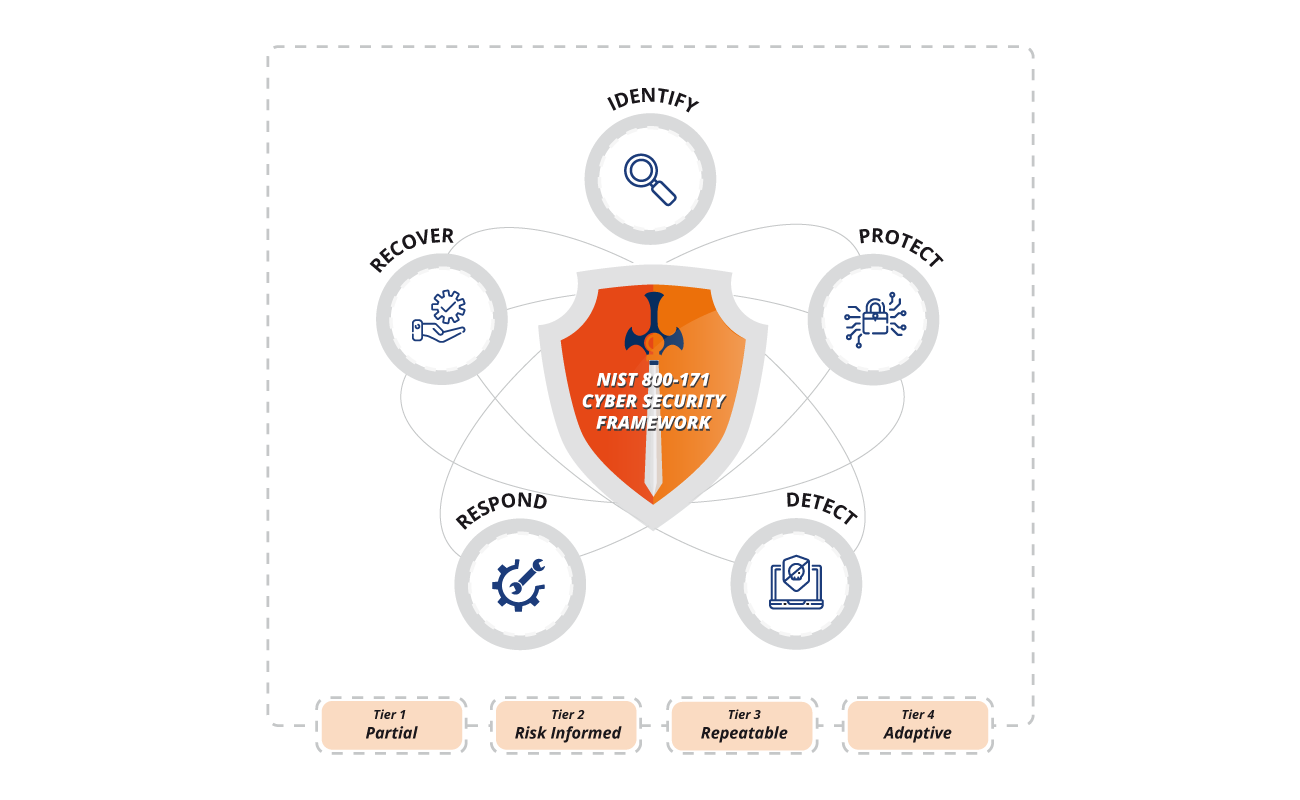
The framework provides a common language and systematic methodology for managing cybersecurity risk. It includes activities to be incorporated in a cybersecurity program that can be tailored to meet any organization’s needs. The framework is designed to complement, not replace, an organization's cybersecurity program and risk management processes. Exhibit below displays the engagement model.
Cyber Security Framework Implementation Approach
- Identify priorities
- Determine compliance requirements
- Review existing policies and practices
- Identify vulnerabilities and risk events
- Identify threats
- Review vulnerabilities
- Define probability & likelihood
- Categorize identified risks
- Create risk heat map
- Identify mitigation approaches
- Define goals for desired outcomes
- Review & outline security priorities
- Translate mitigation into desired outcomes
- Qualify and score current state
- Establish budget and identify resources
- Define targets within budgets
- Share results with stakeholders

Customer Needs is our TOP PRIORITY
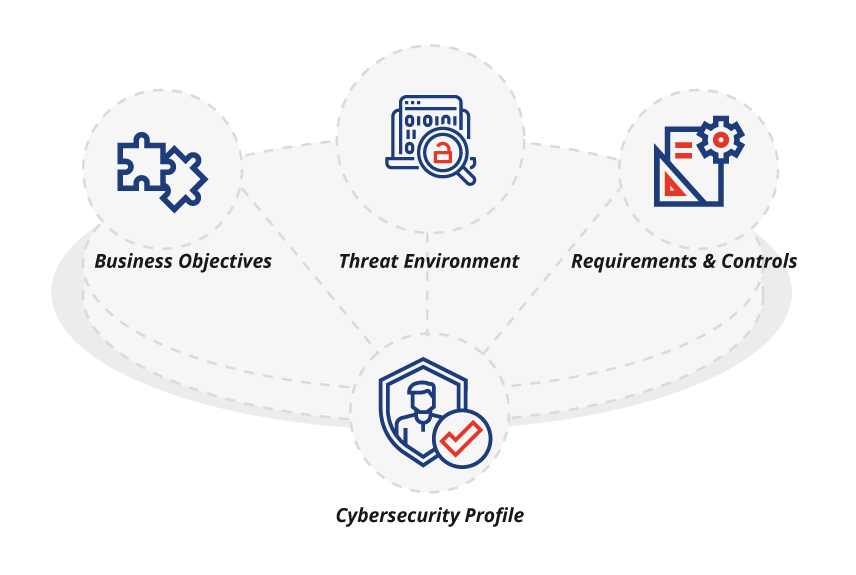
We build the customer’s security profile based on the business objectives of the customer and their existing threats.