Identity is our most precious and irreplaceable asset
As such, its protection is paramount. Safeguarding the identities of individuals, processes, and critical assets requires meticulous attention. Implementing robust privilege controls is essential to mitigate risks and maintain the integrity of our systems.
Accessibility
Access is the lifeblood of business. A single breach can lead to catastrophic consequences, including financial ruin, reputational damage, and even legal repercussions.
Protection
Protect identities seamlessly across all environments – hybrid, SaaS, and multi-cloud – from initial access to final departure. CyberArk’s identity security platform is your impenetrable shield against cyber threats, safeguarding your most valuable assets from unauthorized access.
Security
We simplify access to your data by combining advanced security features. Our solution lets users easily and securely access their information from anywhere, on any device, while protecting against unauthorized entry.
Privilege is everywhere
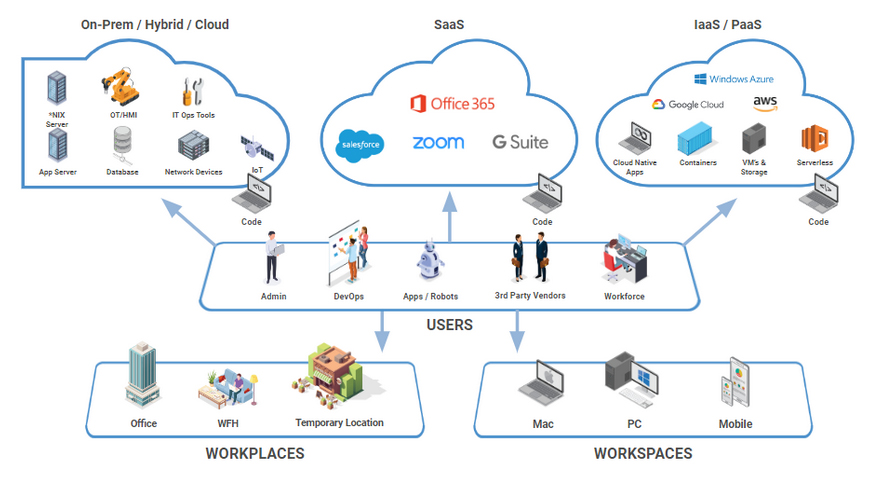
Workforce & Customer Access
We ensure the right people have access to the right data at the right time. By safeguarding employee and customer credentials and tightly controlling access to all systems – on-premise or cloud-based – we protect your critical information.
Identity Management
Streamline identity management across your entire IT system. We automate the creation, management, and analysis of user permissions, ensuring that everyone has the exact access they need and nothing more.
Privileged Access Management
Protect sensitive information across your entire digital landscape. We safeguard privileged credentials and secrets for systems, networks, applications, databases, and cloud environments.
Simple Prescriptive Guidance

Identify Security
Program Framework
Measurably
Reduce Risk

Lessons Learned
in Battle

Full Scope of
Identities
Protect your high-risk users at every turn
We provide comprehensive security across all devices and applications. Gain complete visibility and control over high-risk user activities. Quickly detect unusual behavior, investigate incidents, and streamline audits. Protect sensitive data by recording and auditing all user actions within critical web applications.
Multi-purpose

Understand the
Attack Chain

Assess Your
Security

Manage Cyber
Risk Better

Build Your
Plan
Learning from an attack chain, it is always good to get a clear overview of who has access to what. Easily manage and verify user permissions to ensure ongoing compliance across your entire organization. Boost your enterprise’s security, privacy, and efficiency without sacrificing user experience. We deliver a familiar, personalized workspace while safeguarding your sensitive information. Make data-driven decisions, streamline audits, improve visibility, and ensure compliance through detailed reporting.
