01-Week “#beCyberSmart”
The goal of this theme is to emphasize that cybersecurity isn’t only a shared responsibility. It’s an individual responsibility. If everyone does their part – implementing stronger security practices, raising community awareness, educating vulnerable audiences or training employees, our interconnected world will be safer and more secure for everyone.
As our lives have become increasingly dependent on technology, almost all personal and business data is kept on internet-connected platforms and devices, which can become a gold mine for bad actors. The first full week of Cybersecurity Awareness Month will highlight best security practices and focus on general cyber hygiene to keep your information safe
Own your own role in cybersecurity by starting with the basics
Then take a bold step forward and do something different – look at ways in which you could build a simple cybersecurity framework based on industry standards. This way you can build a strong foundation to be cyber secure and Do Your Part #BeCyberSmart!

Cyber Security Basics
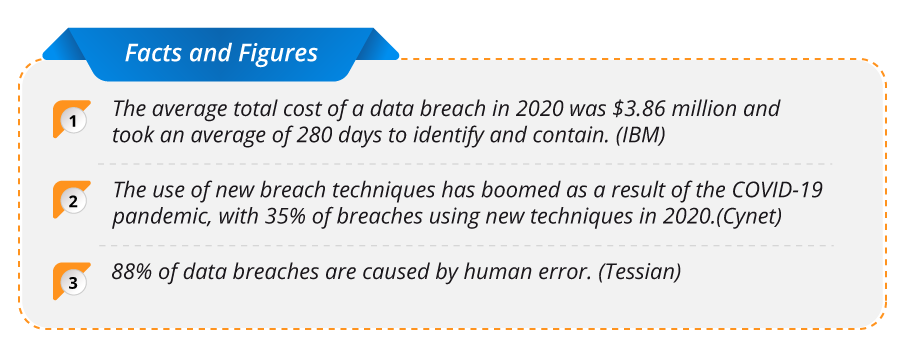
At a time when we are more connected than ever, being “cyber smart” is most important. This year has already seen more than a fair share of attacks and breaches, including the SolarWinds and Kaseya breaches as well as high-profile attacks on the Colonial Pipeline and other critical infrastructure. Cyber attacks have become more sophisticated with new bad actors cropping up each day. They are well organized, collaborate, and share their attack vectors There are several steps that we can take on a daily basis to mitigate risks and stay one step ahead of malefactors.
Use strong passphrases/password manager
This may seem obvious, but too often a strong passphrase/password manager is overlooked. The increased internet usage during the pandemic has certainly contributed to more bad actors prowling for accounts to attack. Complex, and unique passwords are a good way to stop your account from being hacked. Track and remember your password by using a password manager. Check out with Step Ahead how you can use a password manager on a low cost subscription model. Things you can do practically until then
A good password manager could manage these tasks for you. But if you are disciplined and take some extra time to do this, then the above 3 tasks will work.
While this is good, if you are a windows user, you will find that over a period of time, your device becomes very slow, especially when you apply every update Microsoft recommends. Please note that these software updates are general in nature and apply to all versions and product releases which may not be necessary. It depends on what you have enabled in your operating system. Therefore, it makes sense to use an asset manager to keep a tab on your device. Please note that asset managers are a required component of your IT system for compliance. Using an asset manager you can keep a tab on what patches to update, comply with your organization’s security requirements for all devices and ensure that devices in your organization are patched up to the same level and ensure all critical security patches are installed. Check out with Step Ahead on how you could do this most effectively and affordably using a subscription model.
Insight!
- Source from Gartner, Inc.
Worldwide end-user spending on public cloud services is forecast to grow 18.4% in 2021 to total $304.9 billion, up from $257.5 billion in 2020, according to Gartner, Inc.
The pandemic validated cloud’s value proposition, said Sid Nag, research vice president at Gartner.
The ability to use on-demand, scalable cloud models to achieve cost efficiency and business continuity is providing the impetus for organizations to rapidly accelerate their digital business transformation plans. The increased use of public cloud services has reinforced cloud adoption to be the ‘new normal,’ now more than ever.”
The COVID-19 pandemic forced organizations to quickly focus on three priorities: preserve cash and optimize IT costs, support and secure a remote workforce, and ensure resiliency,” said Mr. Nag.
Investing in cloud became a convenient means to address all three of these needs.
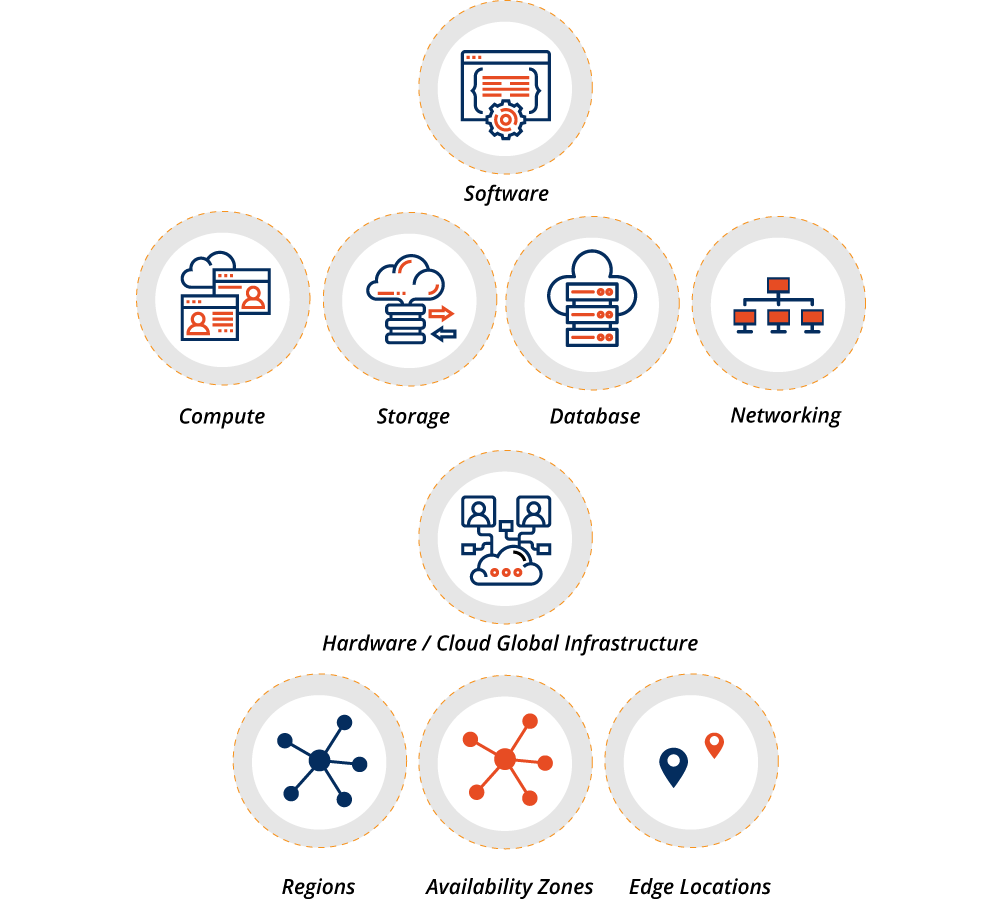
In fact, recent Gartner survey data indicates that almost 70% of organizations using cloud services today plan to increase their cloud spending in the wake of the disruption caused by COVID-19. As enterprises increase investments in mobility, collaboration, and other remote working technologies and infrastructure, Gartner expects growth in public cloud to be sustained through 2024. Let’s accept the inevitable – all of us are using cloud computing in one way or another and that usage is going to grow. And in the cloud, it is always the shared responsibility no matter what cloud based application you use – Microsoft Office, Google Workspace or CRM, etc.
Customer Responsibilities
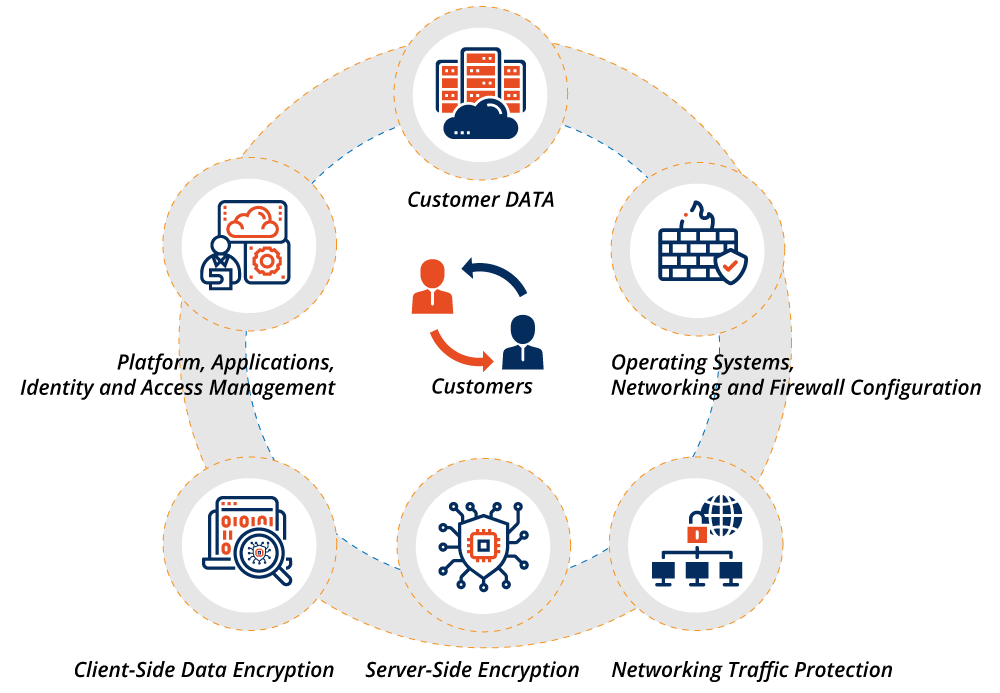
Cloud Service provider Responsibilities